SSL certificate is a digital document that confirms the authenticity of the website and ensures the security of the user's personal data. When using an SSL certificate, data is transmitted to the server via a secure protocol. An SSL certificate consists of a public key and a private key, and may also include a chain of certificates.
If the certificate was not specified when installing the platform, a self-signed SSL certificate will be connected to the platform. When opening the platform's web interface, a warning about a possible security threat will appear in the browser. To prevent this warning from appearing, connect an SSL certificate signed by a certificate authority to the platform.
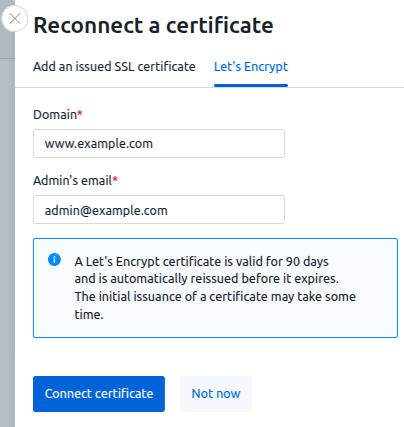
You can purchase a certificate from any certificate issuing service or get a free one from Let's Encrypt. You can get a Let's Encrypt certificate through the platform interface. The platform interacts with Let's Encrypt using the acme.sh script.
A Let's Encrypt certificate is valid for 90 days and is automatically reissued before the expiration date. If you ordered a certificate through the platform interface, the platform will automatically start the renewal process before the certificate expires.
Managing certificates
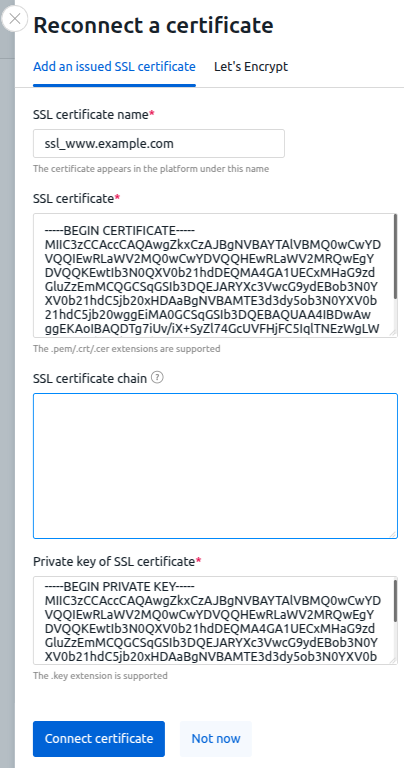
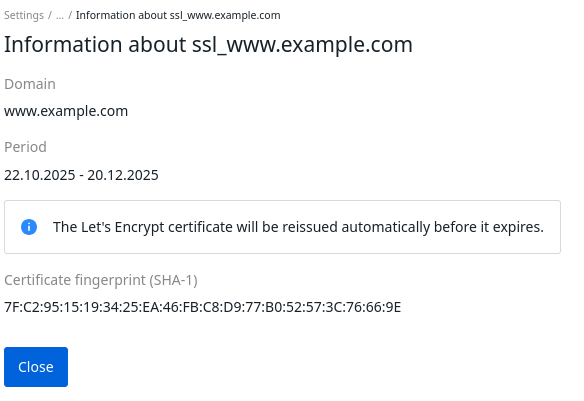
To connect the certificate, in the right menu, click the If the certificate is successfully connected, the If certificate issuance failed, the If the platform fails to automatically reissue the Let's Encrypt certificate, warning banners will appear in the interface. The first banner appears two weeks before the certificate expires, the second one — after the expiration date. To connect another certificate, click the Reconnect the сertificate link and enter the certificate details. To view information about the connected certificate, click the link in the SSL certificate line. In response, you will get the message in the form: Save the received token value. To connect a certificate issued by an Enterprise Certificate Authority on a Windows Server: icon → Global settings tab:
icon → Global settings tab:
 icon will appear in the SSL Certificate line. Some browsers require refreshing the page for this icon to appear.
icon will appear in the SSL Certificate line. Some browsers require refreshing the page for this icon to appear. icon will be displayed next to the certificate name.
icon will be displayed next to the certificate name.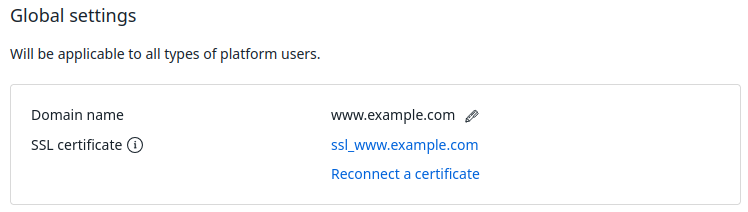
Connecting a certificate via API
curl -k -X POST -H "accept: application/json" -H "Content-Type: application/json" 'https://domain.com/auth/v4/public/token' -d '{"email": "admin_email", "password": "admin_pass"}'{
"confirmed": true,
"expires_at": null,
"id": "6",
"token": "4-e9726dd9-61d9-2940-add3-914851d2cb8a"
}curl --insecure -H 'x-xsrf-token: <token>' -X POST https://example.com/nginxctl/v1/ssl -H 'accept: application/json' -H 'Content-Type: application/json' -d '{"name":"<ssl_name>","certificate":"<ssl_cert>","ca_bundle":"<ssl_bundle>","private_key":"<ssl_private>"}'Connecting a Windows Server certificate
openssl req -new -newkey rsa:2048 -nodes -keyout ssl.key -out ssl.csr
Diagnostics
Certificate issue logs are saved to the /var/log/nginxctl.log file in the input container on the platform server.
Related topics:
 En
En
 Es
Es